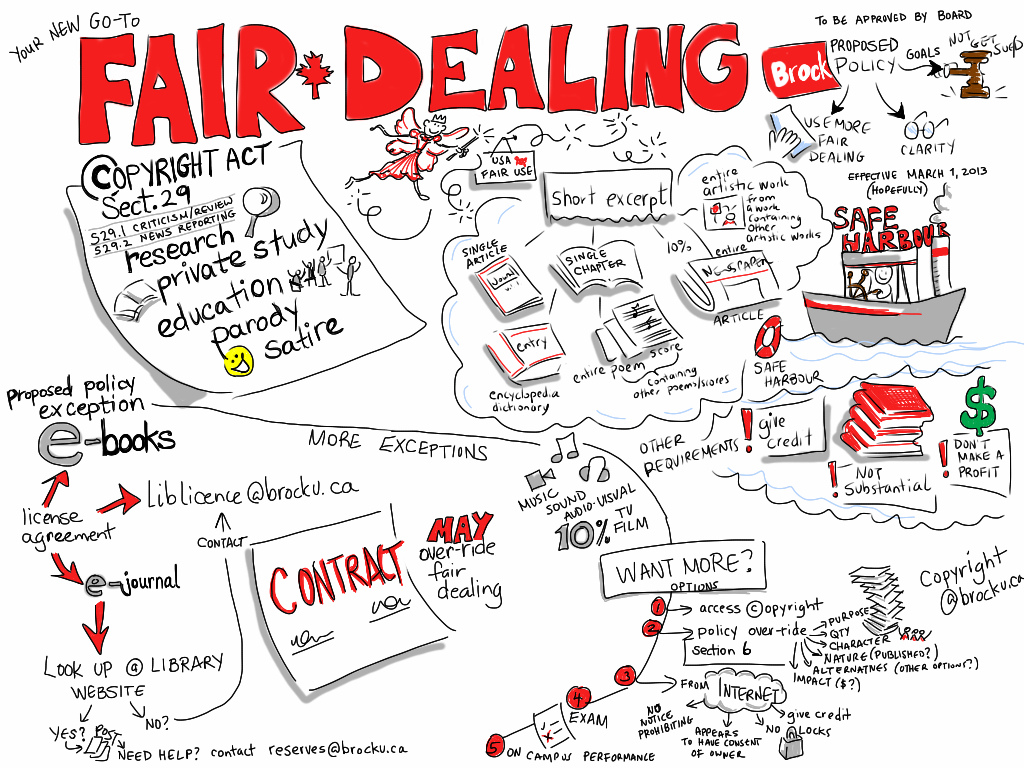
As thousands of children across the province return to school tomorrow, nearly everyone will be asking "what did you do this summer?" If the question were posed to Education Minister Sandra Pupatello, her candid reply might be that she was working with her fellow Provincial Ministers of Education on reforms that will have damaging consequences on Internet use in Canada.
So begins this week's Law Bytes column (Toronto Star version, homepage version) which focuses on the disasterous push from the CMEC to establish a specific educational exception for the use of publicly-available Internet materials. While the CMEC proposal is at least better than Access Copyright's proposed extended license for Internet content (the column reveals that AC has approached Canadian Heritage for funding to support becoming the Canadian collective for the International Standard Text Code – a new standard for "textual works" that can be applied to everything from books to blogs and thus form the basis for a future license), there are potentially several negative long-term effects.
I point to five issues in particular.